Pre-requisites
You can store your AWS keys securely in Jenkins credentials. If you want to interact with AWS from your Jenkins server, you can store your AWS IAM user keys securely in Jenkins rather than openly using the keys in your Jenkins Pipeline. “CloudBees AWS Credentials” Jenkins plugin allows storing AWS IAM user credentials within the Jenkins Credentials API. We can then use these credentials in our pipeline and inject them in the pipeline with the “withCredetinals” step.
Pre-requisites:
“CloudBees AWS Credentials” Jenkins plugin installed on Jenkins server
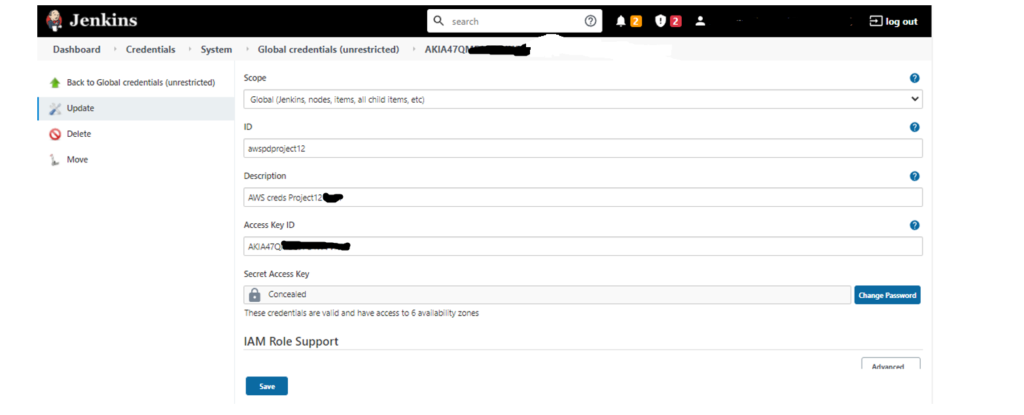
Step 1: Add AWS creds to Jenkins store
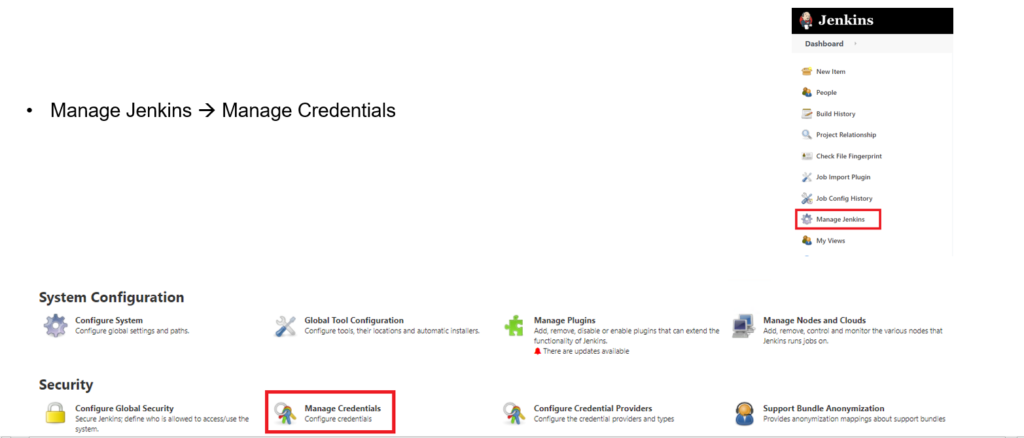
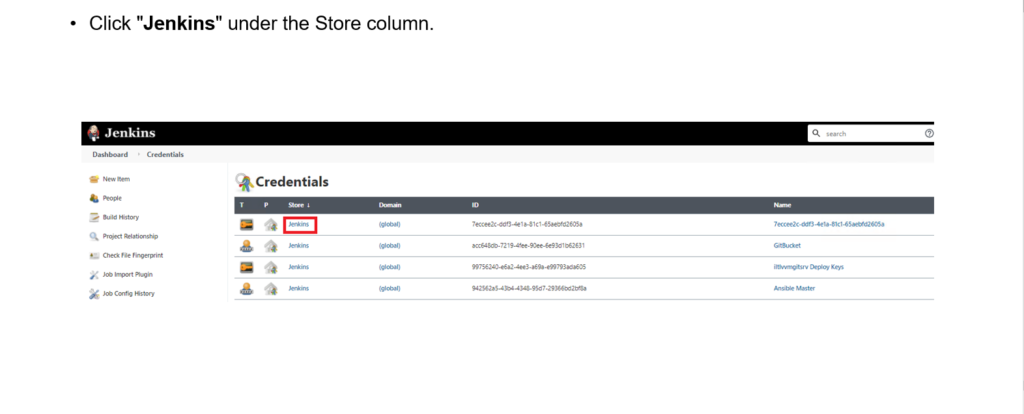
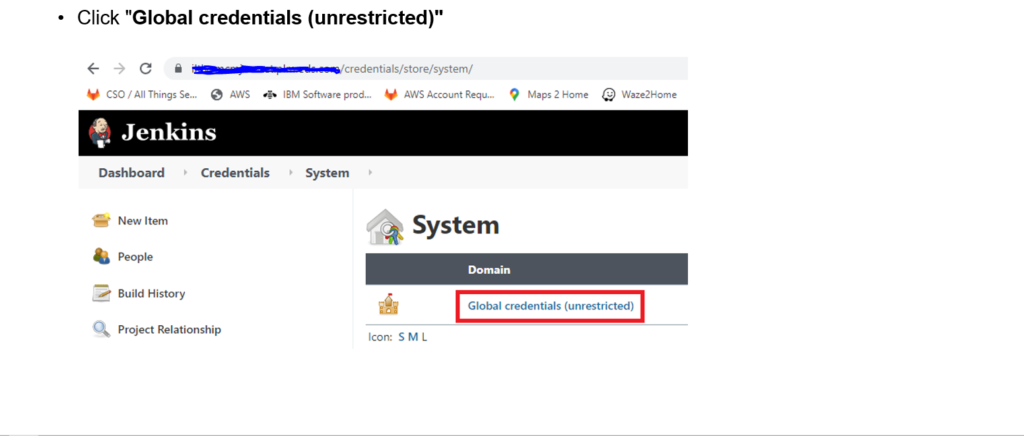

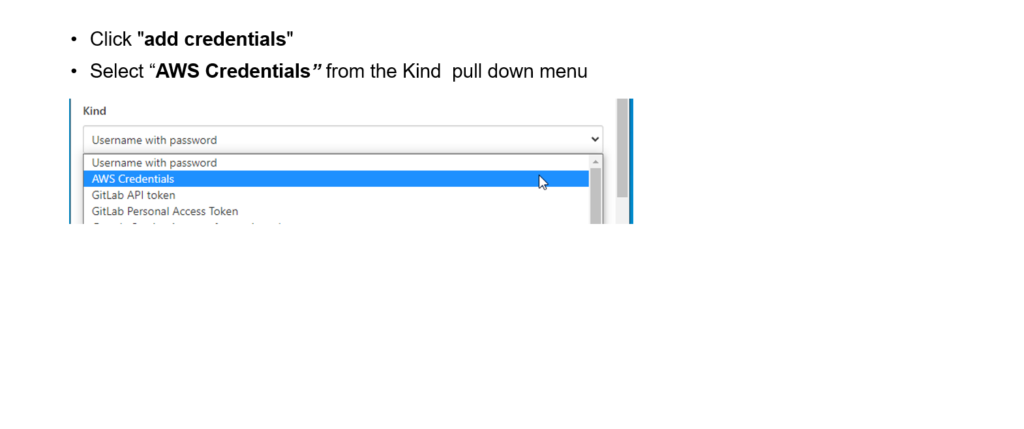
Step 2: Fill the fields: ID, Description, Access Key ID, and Secret Access Key
ID will be used later by function withCredentials(credentials:”<ID>”), e.g.
withCredentials(credentials:“awsdpproject12”)
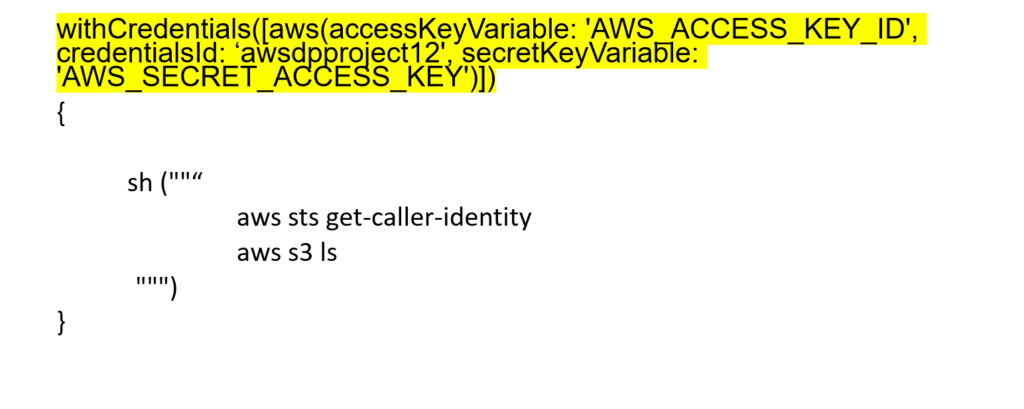
Step 3: use the Groovy syntax of Jenkins in order to use it in the Jenkins pipeline afterward:
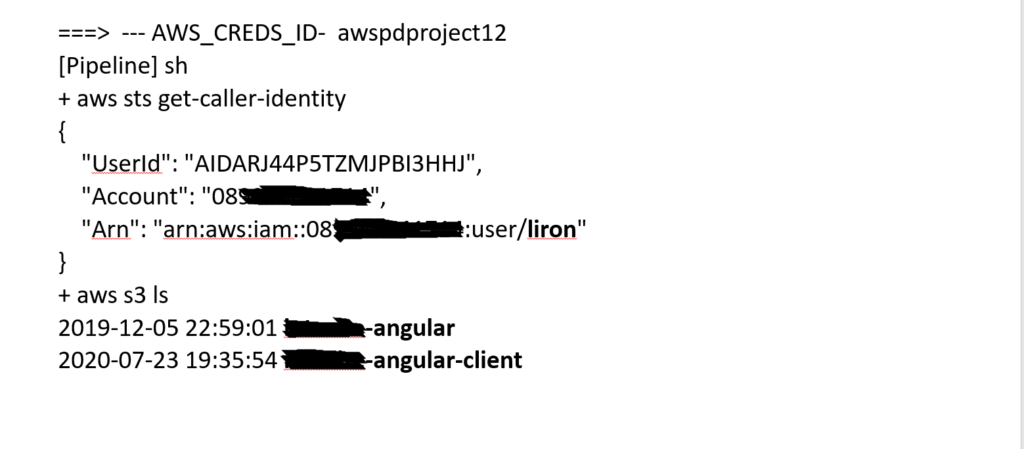
Step 4: Run the Pipeline, verify the output is exact for the right aws account. In my case ” get-caller-identity” will output for me the account info itself. the “aws s3 ls” will pull out the name of S3 buckets that I have in the relevant account
Have Fun 🙂
